2024-08-23
Innovation Highlights
1. The research team proposed a new "confusion-then-proof" technology and designed a novel TLS data authentication protocol that does not require any modifications to the TLS server. It protects data privacy and ensures the authenticity of data sources under the model of a malicious adversary. Experimental results show that the designed protocol increases communication efficiency by 14 times and computational efficiency by 10 times. For example, with Coinbase's Web3 application and Twitter's Web2 application, it has achieved second-level data security authentication in 18 cities worldwide.
2. By leveraging the unique mathematical form of Mersenne primes, a novel and efficient truncation protocol and bit-by-bit comparison protocol were proposed, which can efficiently compute non-linear operator operations in machine learning, such as ReLU, Maxpool, and other activation functions. Experimental results show that the designed protocols have good efficiency and excellent scalability. According to statistics, this is the first protocol framework in the field of privacy-preserving machine learning to achieve such a large number of participating parties. Even in the model of three-party computation, its online phase communication efficiency is at least 1.4 times higher than the previously best Falcon protocol.
Achievements Summary
Web Data Lightweight Certification Based on Confusion-Then-Proof Technology
The Transport Layer Security (TLS) protocol establishes secure channels for most network applications but cannot prove the authenticity of data sources to third parties while protecting data privacy. To address this issue, the DECO protocol published at ACM CCS 2020 used a secure two-party computation under a malicious adversary model to design a TLS data authentication protocol, which does not require any modifications to the TLS server. It ensures the privacy of data and the authenticity of data sources against a malicious adversary but requires considerable communication and computational overhead.
The Yu Yu team proposed a new "confusion-then-proof" technology and designed a novel TLS data authentication protocol that does not require any modifications to the TLS server, achieving the same level of security as the DECO protocol and avoiding the use of secure two-party computation protocols under a malicious adversary model. The security of the proposed protocol has been rigorously proven in both ideal and real models. Experimental results show that the designed protocol increases communication efficiency by 14 times and computational efficiency by 10 times.
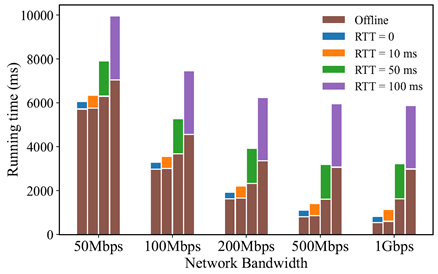
Figure 1. Performance of the Proposed Protocol Under Different Network Bandwidths and Latencies
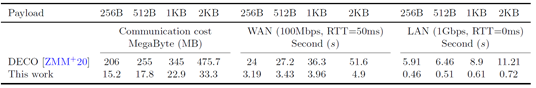
Figure 2. Performance Comparison of the Proposed Protocol with the Previously Most Efficient Protocol DECO
Taking Coinbase's Web3 application and Twitter's Web2 application as examples, second-level data security certification has been achieved in 18 cities worldwide. In addition, an effective method has been proposed to transform the certified TLS data into additive homomorphic commitments, laying the foundation for subsequent applications to implement non-interactive zero-knowledge proofs for TLS data.
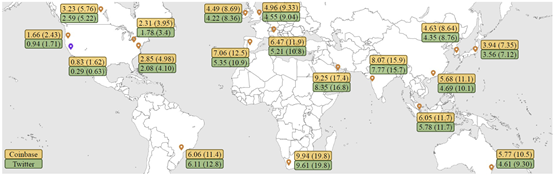
Figure 3. Performance of the Proposed Protocol in Implementing Data Security Certification in 18 Global Cities
The "confusion-then-proof" technology proposed by the Yu Yu team has provided a new design approach for the privacy protection certification of Web2 and Web3 application data, significantly enhancing the performance of previous similar protocols. It has laid a theoretical foundation for the secure migration of Web2 and Web3 application data and provided key technologies. The relevant achievements are included in USENIX Security 2024. The first author of this paper is Xiang Xie, a researcher from the original research institute and a member of PADO Labs.
Privacy-Preserving Machine Learning Protocol Framework Based on Secure Multi-Party Computation Technology
To balance the effective use of data and privacy protection in machine learning, a popular method is to use Secure Multi-Party Computation (MPC) technology to implement Privacy-Preserving Machine Learning (PPML). However, existing protocols mainly focus on settings with 2 to 4 participants. For example, the SecureML protocol framework published at IEEE SP 2017 can securely compute a variety of machine learning algorithms in a two-party setting; the ABY3 protocol framework published at ACM CCS 2018 can implement privacy-preserving machine learning in a three-party setting.
In theory, the Yu Yu team, by leveraging the unique mathematical form of Mersenne primes, based on the famous DN protocol proposed by Damgård and Nielsen in 2007, ensures that the protocol framework can be applied to scenarios involving an arbitrary number of participants. At the same time, the Yu Yu team proposed some efficient MPC primitives, including a truncation primitive with only a 1-bit gap and a fractional multiplication primitive, and a bit-by-bit comparison primitive with no bit gap requirements. These optimized MPC primitives all have only one round of online complexity.
For the truncation primitive, many previous works required the range of input secret values to be much smaller than the modulus size used in the MPC protocol, that is, there is a large gap between the secret values and the modulus values, to ensure the correctness of the truncation result and the statistical security of the protocol. Other works, although they do not require such a gap requirement, have a logarithmic level of round complexity. This work makes full use of the excellent mathematical form of Mersenne primes, that is, the form of p=2^l-1, to reduce the gap between the range of secret values and the modulus size to only 1 bit, while the online round complexity of this truncation protocol is only one round, and the protocol has perfect correctness. A 1-bit gap means that smaller modulus can be used in the MPC protocol or higher computational accuracy can be achieved under the same modulus, thereby directly improving computational and communication efficiency. It is worth noting that this is the first work to optimize the truncation protocol at the theoretical level by utilizing the mathematical properties of Mersenne primes. In addition, this truncation protocol can be well combined with the DN multiplication protocol to obtain a fixed-point fractional multiplication protocol with only one round of online complexity.
For the comparison primitive, many previous works required a large gap or relied on some bit-by-bit operation sub-protocols with logarithmic round complexity. The Yu Yu team proposed a very efficient and simple protocol to calculate the prefix or, whose online stage round complexity is only one round. Specifically, it is achieved by calculating the dual problem of the prefix or problem—the prefix and problem, which can be efficiently calculated through existing prefix multiplication technology. The Yu Yu team further utilized the properties of Mersenne primes to implement an efficient bit-by-bit comparison protocol, which also has an online stage round complexity of one round and has no gap requirements. It should be noted that the bit-by-bit comparison protocol is the foundation for implementing many complex non-linear operations, including precise truncation operations, numerical comparison operations, and widely used ReLU activation functions and Maxpool functions in machine learning.
In terms of application, the Yu Yu team, based on the above-optimized truncation and comparison primitives, proposed a more efficient method for computing non-linear functions (and their gradients), including the widely used ReLU activation function in neural networks and the Maxpool function in convolutional networks (CNNs). In addition, the Yu Yu team conducted privacy inference experiments of neural networks under different numbers of participating parties (from 3 parties to 63 parties). For example, in the setting of 63 participating parties, privacy inference of a 4-layer convolutional neural network, the online stage (preprocessing stage) of the framework takes 0.4 seconds (2.4 seconds) and 4.3 seconds (12.3 seconds) in LAN settings and WAN settings, respectively. According to statistics, this is the first protocol framework in the PPML field to achieve such a large number of participating parties. Moreover, even in the model of three-party computation, its online phase communication efficiency is at least 1.4 times higher than the previously best Falcon protocol.
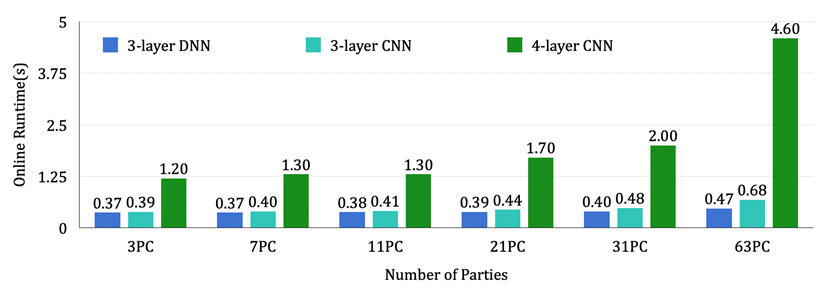
Figure 4. Online Time for Single Privacy Inference of the Proposed Protocol in LAN Settings
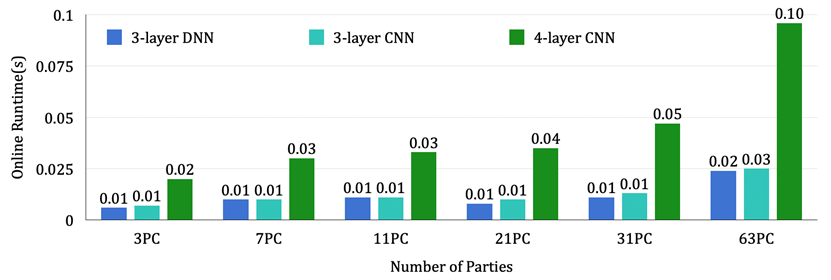
Figure 5. Online Time for Single Privacy Inference of the Proposed Protocol in WAN Settings
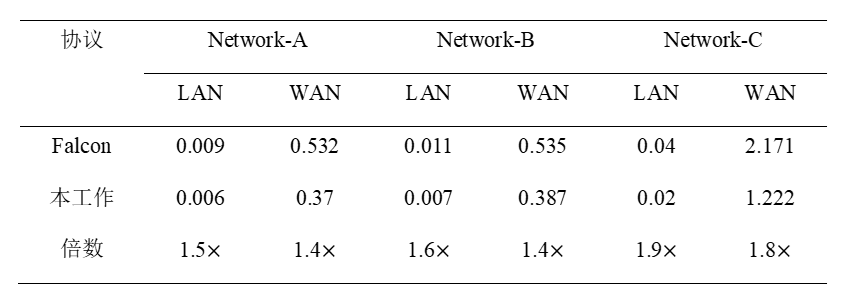
Figure 6. Performance Comparison of the Proposed Protocol with the Previously Most Efficient Falcon Protocol in a Three-Party Setting
This work is the first to optimize the truncation and comparison primitives using the unique mathematical properties of Mersenne primes. These optimized MPC primitives can be directly used as a black box in all MPC applications based on the DN protocol. The reviewers commented: "the paper challenges the state-of-the-art truncations and comparisons that have basically been set up 13 years ago."; At the same time, this work is also the first to implement a privacy inference protocol framework in the PPML field with a large number of participating parties, laying the foundation for further achieving efficient privacy training in large-scale party settings. The relevant achievements are included in USENIX Security 2024. The first author of this paper is Fengrun Liu, an intern at the research institute and a master's student at the University of Science and Technology of China.
For more information, please refer to the paper:
1. Lightweight Authentication of Web Data via Garble-Then-Prove, Xiang Xie, Kang Yang, Xiao Wang, Yu Yu, https://www.usenix.org/system/files/sec24fall-prepub-849-xie-xiang.pdf, USENIX Security 2024.
2. Scalable Multi-Party Computation Protocols for Machine Learning in the Honest-Majority Setting, Fengrun Liu, Xiang Xie, Yu Yu,
https://www.usenix.org/conference/usenixsecurity24/presentation/liu-fengrun.pdf, USENIX Security 2024.